Dan Kaminsky‘s discovery of a nasty bug in DNS rocked the security world in 2008.
It’s now 2010, so you would be forgiven for thinking that most DNS servers should have been updated, patched or configured in such a manner as to render the Kaminsky hole null and void.
Unfortunately that is not the case.
Several medium sized DNS providers, which include ISPs, data centre providers and many others, are still operating DNS servers that are vulnerable according to the IANA test
So what is the danger?
The danger is what is called “cache poisoning“. In simpler terms, it is possible for a criminal to take advantage of a nameserver‘s configuration and conduct either a “man in the middle” type attack or simply to redirect all the traffic elsewhere. The number of issues is only limited by the criminal’s imagination and technical skill.
Here’s but one example using boards.ie (a popular forum in Ireland) :
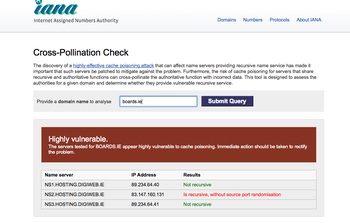
UPDATE: Digiweb have fixed their DNS configuration so the test above will no longer work.


Not really sure what’s going on here. My attack was against caches. These servers are not caches — they store the authoritative data that _other hosts_ cache.
It may happen that an authoritative server also caches for other authorities. It may even be the case that this is considered “bad form” by some people.
But it’s never the case that “individual domains” are vulnerable to my attack. If a user is using one of these servers as a recursive cache, and it’s unpatched, then there’s a problem for every domain in the world (for that user). If not, no problem.
Dan
Thanks for taking the time to post a comment.
Some of the nameservers that were identified to us in a confidential email were resolvers, so how they were being used or potentially abused is a big nasty question mark.
Of course you are 100% right. An individual domain in itself wouldn’t be “vulnerable”.
Thanks for your comment
Michele
I’m the founder of Boards.ie
I dont know whats going on here either but since Michele is a competitor to our host (Digiweb) I have my own views.
Michele, either clarify this or remove us as your “example”. I’m furious you have used us in this way when the author of the exploit has said, right here, it doesn’t apply.
Tom.
Tom
I think you have picked up the wrong end of the stick entirely. Unless someone is using boards.ie as a DNS provider they wouldn’t be impacted in any way.
Your DNS provider had not addressed the issue with recursive DNS earlier today – even though it has been a known issue for nearly two years.
They seem to have finally resolved this now, so I will update the post accordingly.
I will not be removing the example.
Regards
Michele